IPv4 Network Audit
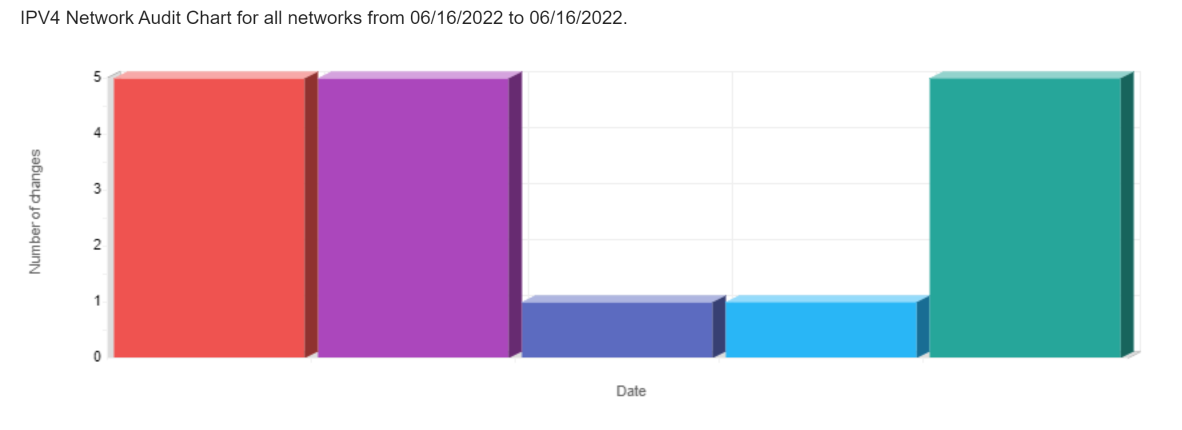
Conducting an IPv4
Network Audit is crucial for network security, compliance
adherence, troubleshooting, accountability, and capacity planning.
It offers a comprehensive log of network activities, serving
multiple purposes. This audit ensures accountability by tracking
administrator actions, detecting errors, and preventing malicious
behavior. It also aids in network capacity planning by analyzing
usage patterns and identifying areas that require optimization or
upgrading. Moreover, it assists in meeting compliance requirements
as many regulatory bodies mandate a thorough record of network
operations. Additionally, the audit report facilitates issue
resolution by pinpointing the root cause, providing detailed
information on network changes and their respective timing,
enabling effective troubleshooting.
IPv4 Subnet Audit By Address

The IPv4 Subnet Audit
By Address report is vital for subnet security, compliance
adherence, troubleshooting, accountability, and capacity planning.
It offers a comprehensive log of all subnet activities, serving
various purposes. Regulatory bodies often mandate organizations to
maintain such records for audits. When subnet issues arise, the
audit report aids in pinpointing the cause by detailing the who,
what, and when of subnet changes, facilitating effective
troubleshooting. Maintaining accountability, the report detects
administrator errors and prevents malicious activities.
Additionally, it reveals subnet usage patterns, enabling
organizations to optimize or upgrade specific areas based on
analysis of the audit report.
IPv4 Subnet Audit By Group
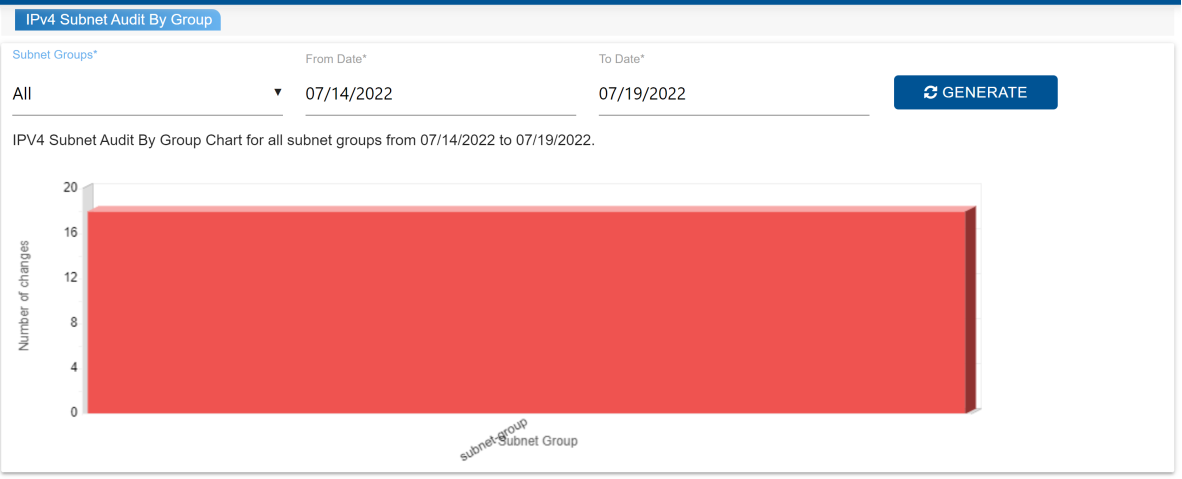
The IPv4 Subnet Audit
By Group report is crucial for maintaining subnet group security
and integrity, meeting compliance requirements, troubleshooting,
ensuring accountability, and planning capacity. It serves as a
comprehensive record of all subnet group operations, serving
various purposes. Compliance regulations often mandate
organizations to maintain such records for auditing. When issues
arise, the audit report pinpoints the cause by detailing changes
made, who made them, and when. This aids troubleshooting and
resolution. Additionally, tracking subnet group operations fosters
accountability, exposing errors and preventing malicious
activities. Furthermore, the report reveals subnet group usage
patterns, aiding capacity planning by identifying areas that
require optimization or upgrading.
IPv4 Subnet List By Group
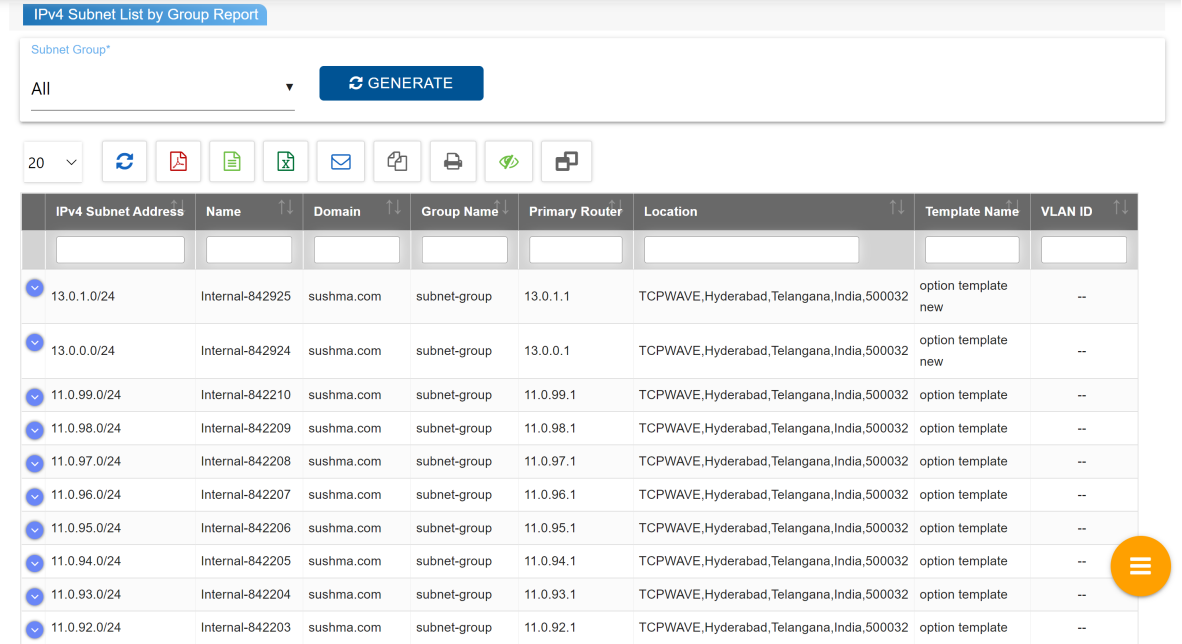
The IPv4 Subnet List
by Group report is crucial for subnet management, planning,
troubleshooting, compliance, and accountability. It offers a
comprehensive list of subnets within a subnet group or all groups,
serving diverse purposes. This report facilitates network
administrators in efficiently overseeing and controlling subnets
by providing a consolidated list. It aids in planning by revealing
subnet usage patterns and capacity assessment. Troubleshooting
becomes easier as the report presents a comprehensive list of
subnets, enabling prompt resolution of issues. Furthermore, it
supports compliance requirements by documenting all subnets, a
vital aspect for regulatory audits. Lastly, the report ensures
accountability by detailing subnet changes and their timestamps,
discouraging errors and malicious activities.
IPv4 Subnet Template Audit
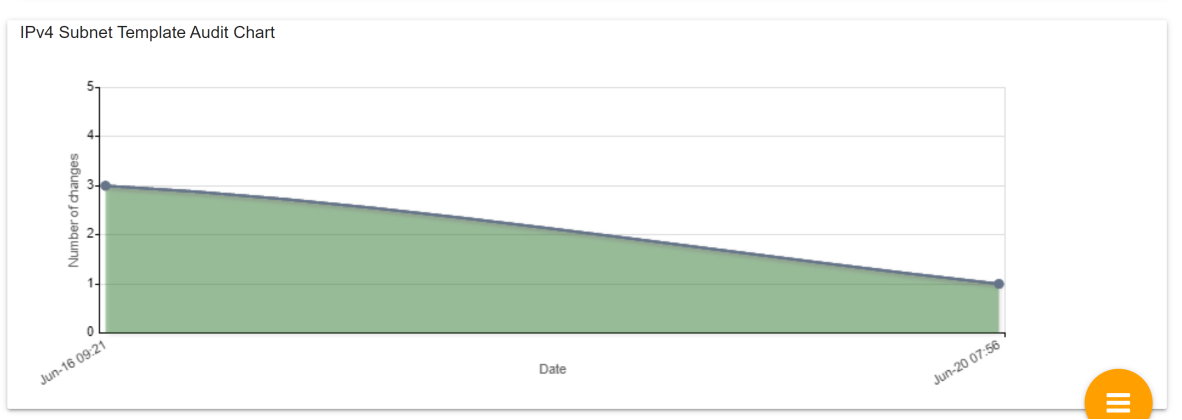
Subnet templates are
vital for managing subnets, ensuring consistent IP address
allocation and minimizing errors. The audit history report tracks
template changes, detecting unauthorized modifications that
compromise network security. This documented history aids future
reference, analysis, and reporting, protecting the network's
integrity. Subnet templates streamline IP address management,
applying key parameters to multiple subnets. The audit report
monitors changes, identifying security breaches. It serves as a
resource for maintaining security and compliance. With subnet
templates, administrators simplify network administration. The
audit report enables detailed reporting and effective
communication. It fosters accountability and ensures policy
compliance. In summary, subnet templates and the audit report
enhance network security and efficiency.
IPv4 Object Audit

The IPv4 Object Audit
report offers a comprehensive record of actions performed by an
administrator on a specific object. In the context of IPv4
addressing, an object can refer to a network or host IP address,
name, or IP address range. This report supplies detailed data on
object modifications, aiding network administrators in monitoring
changes, troubleshooting problems, and upholding network security.
It includes information about the individuals responsible for the
changes, the nature of the changes, and the timing of the changes.
Moreover, the report tracks actions like object addition or
removal, property modifications, and status changes, while also
granting administrators the ability to specify a desired date
range for tracking object changes within that period.
IPv4
Object End Of Life

End of Life (EOL)
refers to the point when a product or service is no longer
supported by its manufacturer, lacking updates, bug fixes, and
technical assistance. This leaves users exposed to security
vulnerabilities, compatibility issues, and other risks. The
TCPWave End of Life Report is a valuable tool for identifying
objects nearing the end of their life span, specifically in IP
address management. It provides crucial information like object
name, type, current status, EOL date, and remaining days until
expiration. This report aids network administrators in efficiently
managing their resources by taking necessary actions to ensure
network availability and integrity. Through renewals, updates, or
removals, administrators can prevent security breaches, network
downtime, and other risks tied to expired resources.
IPv4 Object Audit By MAC Address
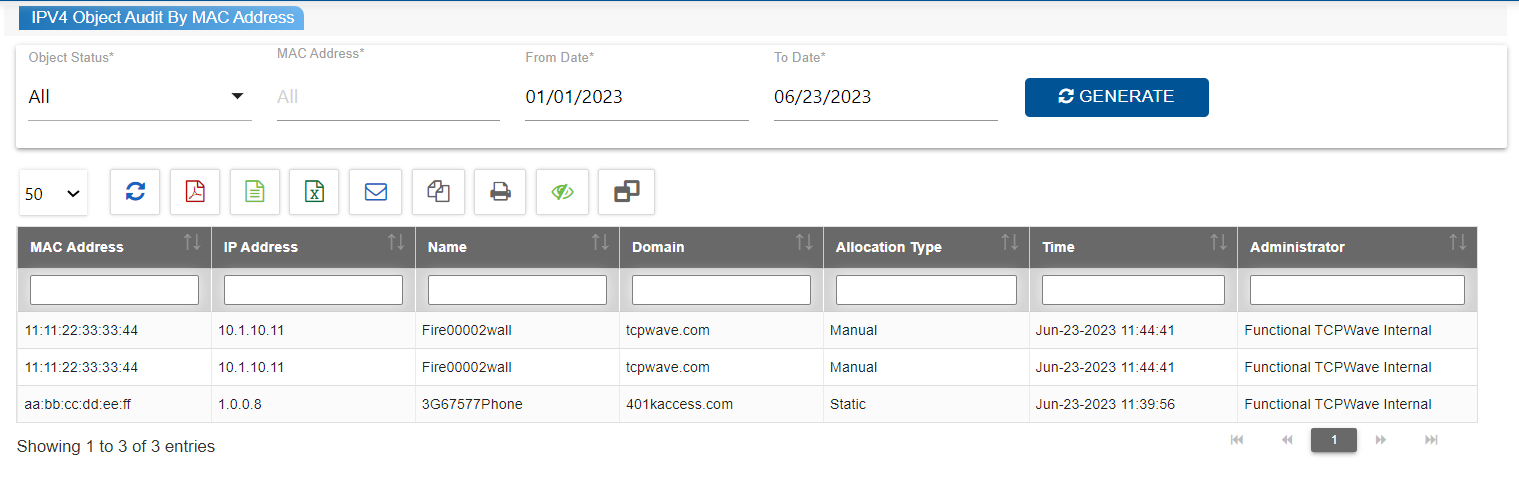
The IPv4 Object Audit
Report by MAC Address is a detailed record of MAC address
associations with IPv4 objects, such as hosts or network
addresses, for a specified period. It captures all operations
related to MAC addresses, including additions, edits, and
deletions during the designated timeframe. This report assists
administrators in troubleshooting and maintaining network security
by tracking changes made to MAC addresses. Additionally,
administrators can select specific date ranges to monitor
modifications made to MAC addresses associated with objects within
that timeframe. Overall, this report offers crucial insights for
network management and security purposes, providing a centralized
and comprehensive overview of MAC address activities.
IPv4 Appliance Configuration Audit
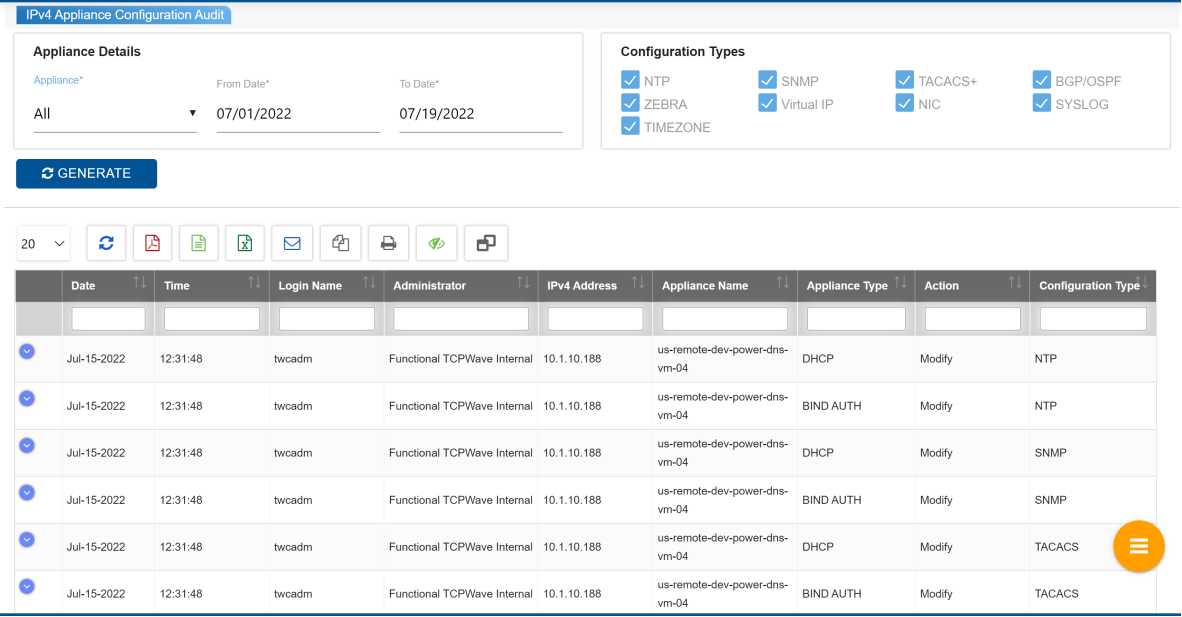
The IPv4 Appliance
Configuration Audit report offers a comprehensive record of
configuration changes made to each appliance. It furnishes
extensive details on the appliance configuration, aiding in issue
troubleshooting and network security maintenance. The report
covers essential information like the initiator, nature, and
timing of the alterations. It diligently tracks changes involving
addition, modification, or removal of configurations for each
appliance, assisting administrators in troubleshooting and
ensuring network security. Furthermore, administrators have the
flexibility to choose a specific date range for monitoring
appliance configuration changes within that period.
IPv4 Reclaimable Objects Report
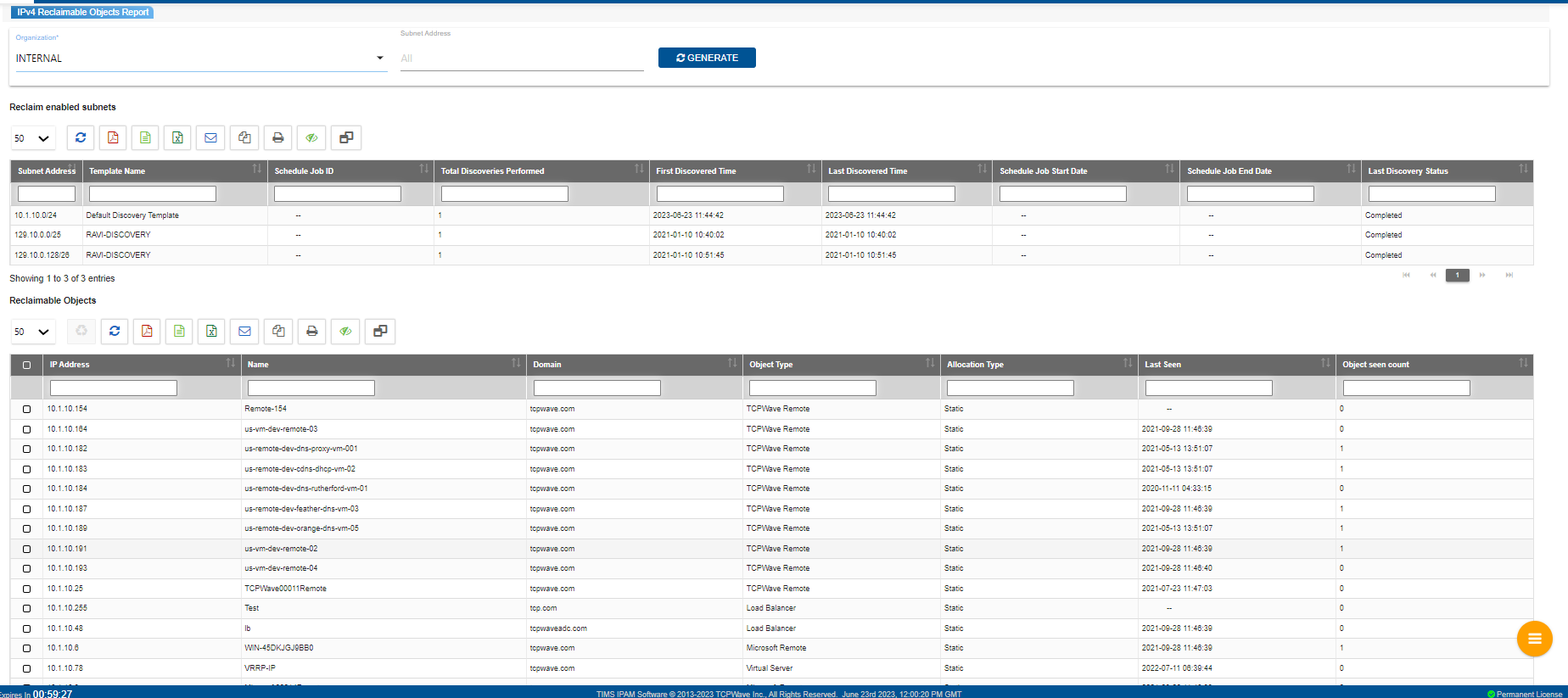
The IPv4 Reclaimable
Objects Report is an analysis of IPv4 subnets, pinpointing any
reclaimable objects within them. It aids network administrators in
recognizing unused IP addresses, networks, or ranges that can be
reclaimed for reuse. The report offers comprehensive details on
subnet usage, enabling the identification of unused networks or
ranges that can be reclaimed. By identifying and reclaiming unused
IP resources, such as addresses, networks, and ranges,
administrators can optimize IP utilization and minimize the need
for additional address assignments. The audit report includes two
grids: one showcasing information about reclaim-enabled subnets
and the other displaying details of reclaimable objects.
IPv4 Overlapping Address Space
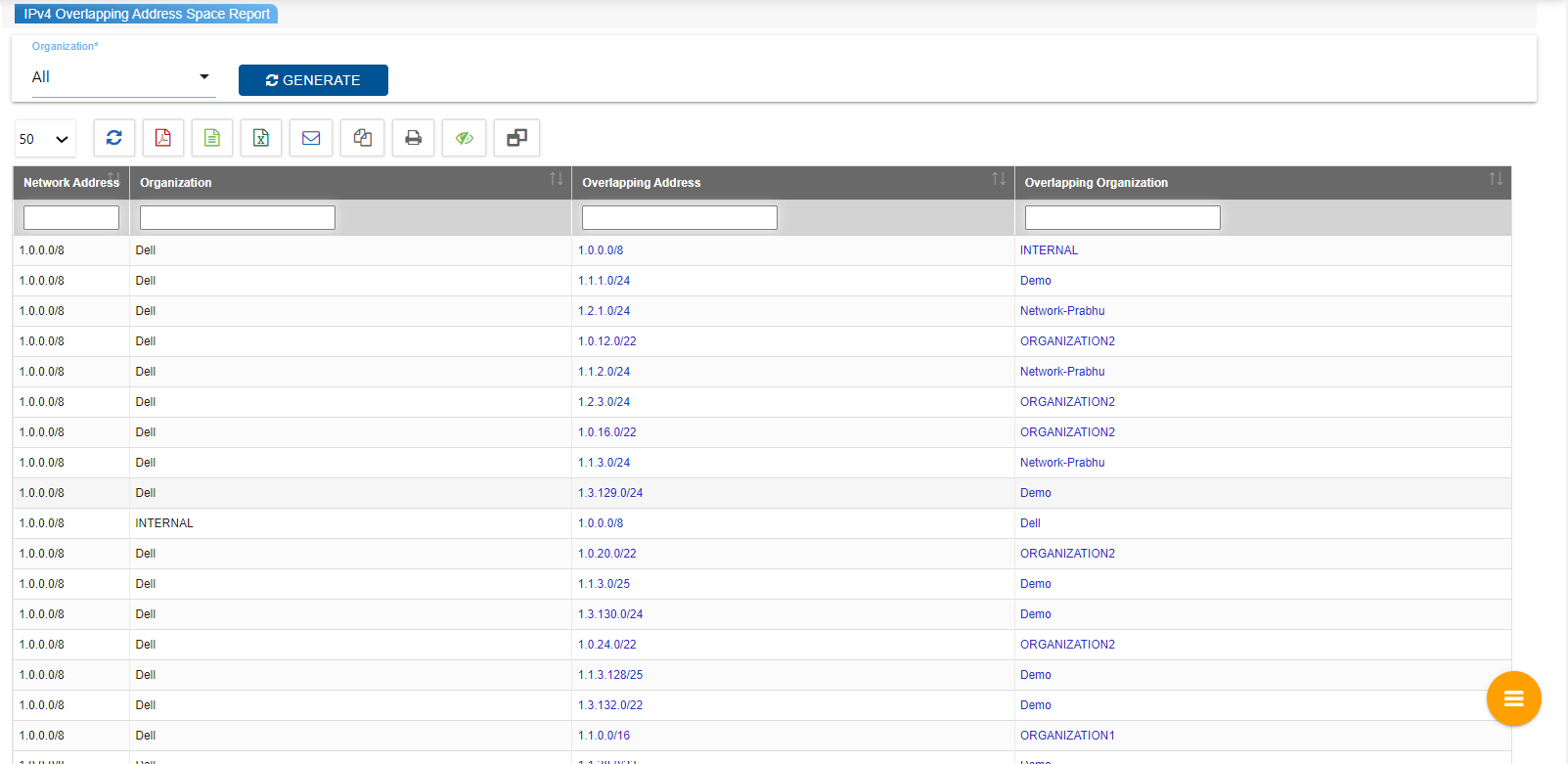
IPv4 Overlapping Address
Space Report help network administrators identify overlapping IP
address ranges in different organizations. The report provides a
snapshot of the current state of overlapping IP addresses and can
help in troubleshooting and preventing connectivity issues. The
report contains details of the overlapping IP address spaces in
different organizations. The administrator can select the option
"ALL" to view details of all the organizations or choose specific
organizations from the organization dropdown menu. By doing so,
the administrator can identify which organizations are using
overlapping IP address ranges and take appropriate actions to
resolve the issue. Overlapping Address Space Report is a useful
tool for network administrators to identify and address IP address
conflicts, which can improve network connectivity and performance.
IPv4 Available Subnets

IPv4 Available Subnets
Report provides a list of available subnets that have not been
created in a given network for a particular organization. The
report helps the network administrator to create new subnets and
analyze network space availability. It shows which IP addresses
are available for use and which ones are already in use, allowing
the administrator to allocate IP addresses efficiently. The report
typically includes information such as the network address, subnet
mask, number of hosts per subnet, and the number of subnets
available for use. The administrator can use this information to
determine the appropriate subnet mask and the number of hosts
required for each subnet. IPv4 Available Subnets Report is a
useful tool for network administrators to manage IP address
allocation efficiently, ensuring that all devices on the network
have a unique IP address and reducing the risk of IP address
conflicts.























